Web scraping, the process of extracting data from websites, is a powerful tool for gathering information. However, sometimes the most efficient and reliable way to access data lies hidden beneath the surface – in the form of undocumented APIs.
The Power of APIs: Efficiency and Reliability
Application Programming Interfaces (APIs) offer a structured and efficient way to interact with websites and retrieve data. They often provide access to data that is not publicly available through the website’s user interface, and they can offer significantly faster data retrieval compared to scraping.
The Hidden API: A Treasure Trove of Data
While many websites openly document their APIs, others keep them hidden, either intentionally or unintentionally. These hidden APIs can be a valuable resource for data extraction, offering efficient access to structured data.
Finding the Hidden Gem: A Detective’s Approach
Uncovering hidden APIs requires a bit of detective work. Here’s a step-by-step guide:
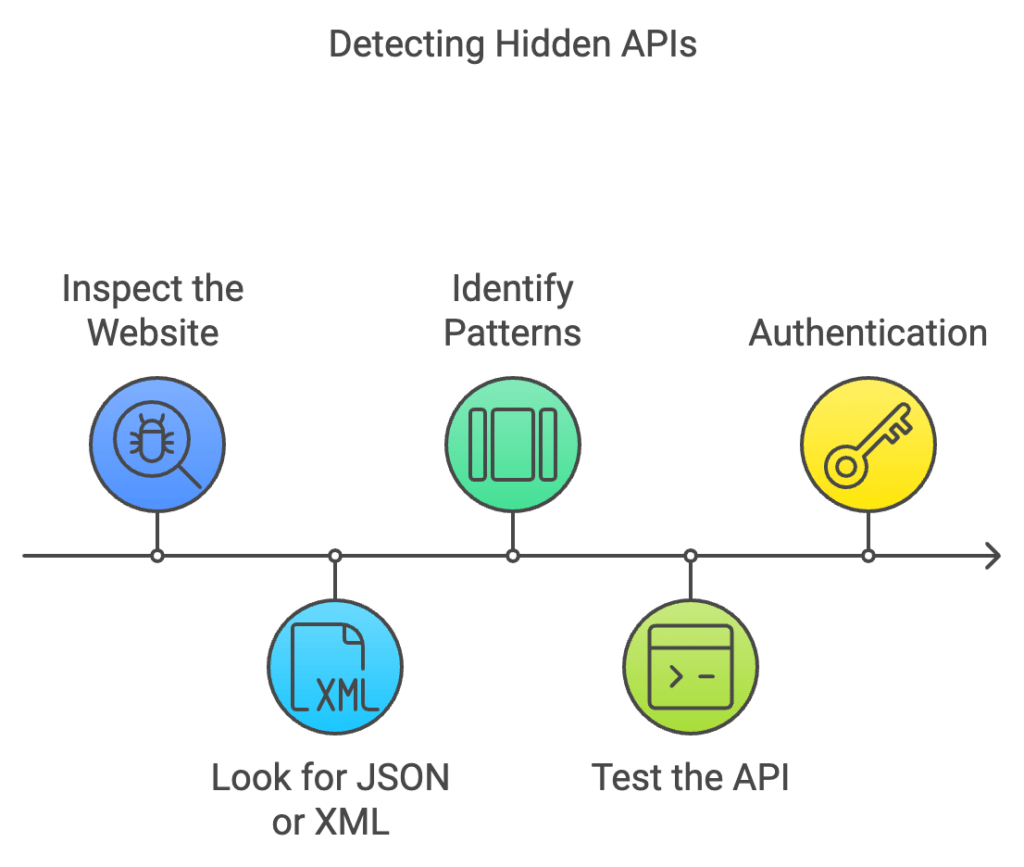
- Inspect the Website: Use your browser’s developer tools (usually accessed by right-clicking and selecting “Inspect”) to examine the website’s HTML source code.
- Look for JSON or XML: Pay close attention to any dynamically loaded content or embedded data. JSON (JavaScript Object Notation) and XML (Extensible Markup Language) formats often signal the presence of an API.
- Identify Patterns: Examine the structure of the JSON or XML data. Look for repeating patterns or identifiers that suggest a consistent data format.
- Test the API: Once you’ve identified a potential API endpoint, test it using tools like curl in your terminal or a web API testing tool like Postman.
- Authentication: Many hidden APIs require authentication. You may need to analyze the website’s login process or examine network requests to identify authentication tokens or cookies.
Beyond the Basics: Handling Authentication and Access
- Direct Access: In rare cases, you might be able to access a hidden API directly without authentication, but this is uncommon.
- Emulating Real Devices: To access protected APIs, you can copy the headers and cookies from a real browser session to mimic a legitimate user request. This technique can be used to bypass basic authentication checks.
- API Keys and Tokens: Many APIs require an API key or token for access. These are often obtained through registration or application processes.
Ethical Best Practices
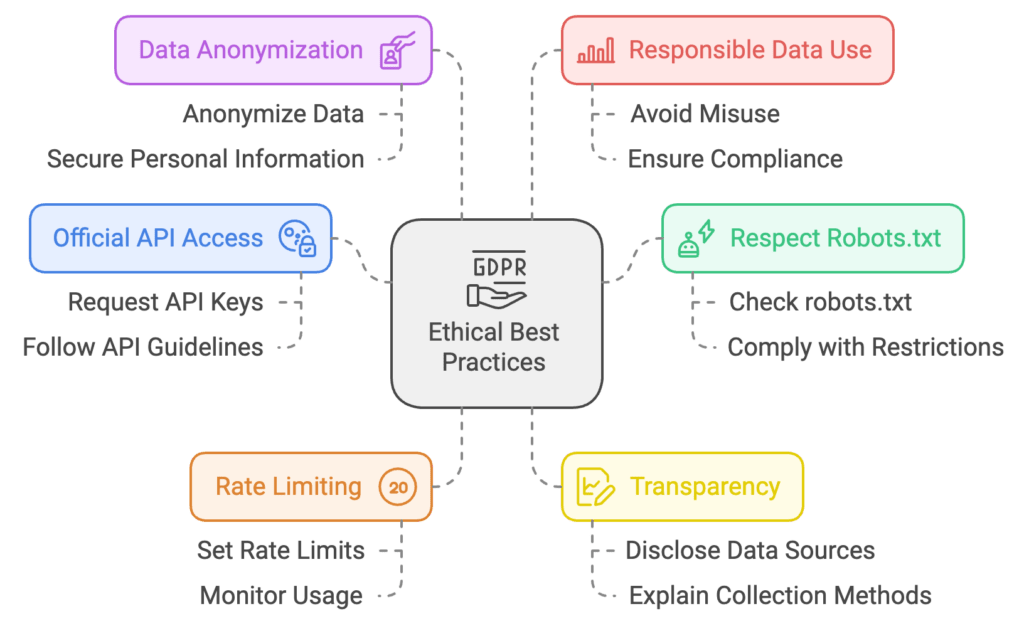
- Seek official API access where possible.
- Respect robots.txt and publicly stated usage policies.
- Implement reasonable rate limiting to minimize impact on servers.
- Be transparent about data sources and collection methods.
- Anonymize and protect any personal data collected.
- Use collected data responsibly and ethically.
Need Help Unlocking Hidden Data?
If you’re struggling to find and access hidden APIs, We can help! Our data linking service specializes in extracting data from both public and hidden APIs, providing you with the information you need efficiently and reliably.
Related Articles: